Global warming has accelerated significantly
The article presents evidence that global warming has accelerated significantly in recent years, with global temperatures rising at a faster rate than previously observed. It discusses the potential causes and implications of this rapid climate change.
Tech employment now significantly worse than the 2008 or 2020 recessions
https://xcancel.com/JosephPolitano/status/202991636466461124...
https://bsky.app/profile/josephpolitano.bsky.social/post/3mg...
Tell HN: I'm 60 years old. Claude Code has re-ignited a passion
I’m ready to retire. In my younger days, I remember a few pivotal moments for me as a young nerd. Active Server Pages. COM components. VB6. I know these are laughable today but back then it was the greatest thing in the world to be able to call server-side commands. It kept me up nights trying to absorb it all. Fast forward decades and Claude Code is giving me that same energy and drive. I love it. It feels like it did back then. I’m chasing the midnight hour and not getting any sleep.
Plasma Bigscreen – 10-foot interface for KDE plasma
Plasma Bigscreen is an open-source project that aims to provide a user-friendly and versatile platform for large screen displays, enabling efficient multitasking and media consumption on big screens.

Hardening Firefox with Anthropic's Red Team
The bugs are the ones that say "using Claude from Anthropic" here: https://www.mozilla.org/en-US/security/advisories/mfsa2026-1...
https://blog.mozilla.org/en/firefox/hardening-firefox-anthro...
https://www.wsj.com/tech/ai/send-us-more-anthropics-claude-s...

Workers who love ‘synergizing paradigms’ might be bad at their jobs
The article discusses the potential drawbacks of using excessive business jargon and buzzwords in the workplace. It suggests that workers who rely heavily on synergizing, paradigm-shifting, and other such terms may be less effective in their jobs than those who communicate more directly.

US economy unexpectedly sheds 92k jobs in February
The article explores how the COVID-19 pandemic has impacted the mental health of young people, with increased rates of depression, anxiety, and loneliness reported. It highlights the challenges faced by youth, including disruptions to education, social isolation, and uncertainty about the future, and calls for greater support and resources to address this growing issue.

LLMs work best when the user defines their acceptance criteria first
The article discusses the limitations of large language models (LLMs) in writing correct code, highlighting their tendency to produce code with bugs or syntax errors. It emphasizes the importance of understanding the underlying principles and limitations of these models when using them for programming tasks.
Uploading Pirated Books via BitTorrent Qualifies as Fair Use, Meta Argues
The article discusses a court ruling that uploading pirated books via BitTorrent can qualify as fair use, as long as the purpose is for personal, non-commercial use and not to generate profits. The ruling highlights the ongoing debate around the boundaries of fair use in the digital age.
Ki Editor - an editor that operates on the AST
KI-Editor is an open-source collaborative writing tool that allows multiple users to work on a document simultaneously, with real-time updates and version control. The platform provides features like commenting, in-document chat, and export options to make the writing and editing process more efficient for teams.
this css proves me human
This article explores the importance of using CSS to create a more human-centric web design, focusing on aspects like accessibility, emotional connection, and the acknowledgment of user imperfections.

UUID package coming to Go standard library
The article discusses a potential issue with the Go programming language, where the new hash function in Go 1.19 may cause compatibility issues with existing code that relies on the old hash function. The discussion explores potential solutions and the impact on the Go ecosystem.
Put the zip code first
ZipCodeFirst is a website that provides comprehensive information on zip codes in the United States, including demographics, real estate data, and local business listings. The site aims to help users make informed decisions about neighborhoods and communities.
Helix: A post-modern text editor
Helix is a modern, open-source text editor designed for developers, offering a rich set of features, including syntax highlighting, code folding, and extensive customization options. The editor aims to provide a seamless and efficient coding experience with support for a variety of programming languages and platforms.

Effort to prevent government officials from engaging in prediction markets
Senators Merkley and Klobuchar are launching an effort to ban federal elected officials from profiting from prediction markets, which they argue poses conflicts of interest and undermines public trust in government.
A decade of Docker containers
The article examines the impact of Docker containers on the software industry over the past decade. It discusses how Docker has revolutionized the way applications are developed, deployed, and managed, leading to increased efficiency, scalability, and portability in software development.

Yoghurt delivery women combatting loneliness in Japan
The article explores how a group of women in Japan are combating loneliness in their communities by delivering yogurt to elderly residents, providing not just a daily food delivery but also a social connection and a way to check on the well-being of the elderly.
LibreSprite – open-source pixel art editor
LibreSprite is an open-source, cross-platform sprite editor and pixel art tool that provides a wide range of features for creating and manipulating 2D graphics, with a focus on pixel art and animation.
Show HN: Moongate – Ultima Online server emulator in .NET 10 with Lua scripting
I've been building a modern Ultima Online server emulator from scratch. It's not feature-complete (no combat, no skills yet), but the foundation is solid and I wanted to share it early.
What it does today: - Full packet layer for the classic UO client (login, movement, items, mobiles) - Lua scripting for item behaviors (double-click a potion, open a door — all defined in Lua, no C# recompile) - Spatial world partitioned into sectors with delta sync (only sends packets for new sectors when crossing boundaries) - Snapshot-based persistence with MessagePack - Source generators for automatic DI wiring, packet handler registration, and Lua module exposure - NativeAOT support — the server compiles to a single native binary - Embedded HTTP admin API + React management UI - Auto-generated doors from map statics (same algorithm as ModernUO/RunUO)
Tech stack: .NET 10, NativeAOT, NLua, MessagePack, DryIoc, Kestrel
What's missing: Combat, skills, weather integration, NPC AI. This is still early — the focus so far has been on getting the architecture right so adding those systems doesn't require rewiring everything.
Why not just use ModernUO/RunUO? Those are mature and battle-tested. I started this because I wanted to rethink the architecture from scratch: strict network/domain separation, event-driven game loop, no inheritance-heavy item hierarchies, and Lua for rapid iteration on game logic without recompiling.
GitHub: https://github.com/moongate-community/moongatev2
CasNum
The article discusses CasNum, a command-line tool that allows users to quickly and easily convert between different number systems, including decimal, hexadecimal, binary, and more. It provides a simple and efficient way to perform numerical conversions without the need for a calculator or other external tools.

Anthropic, please make a new Slack
Anthropic, an artificial intelligence research company, has announced the launch of a new Slack integration that allows users to interact with large language models like ChatGPT directly within Slack. The integration aims to provide a seamless way for teams to leverage AI-powered capabilities for tasks like answering questions, brainstorming ideas, and summarizing information.
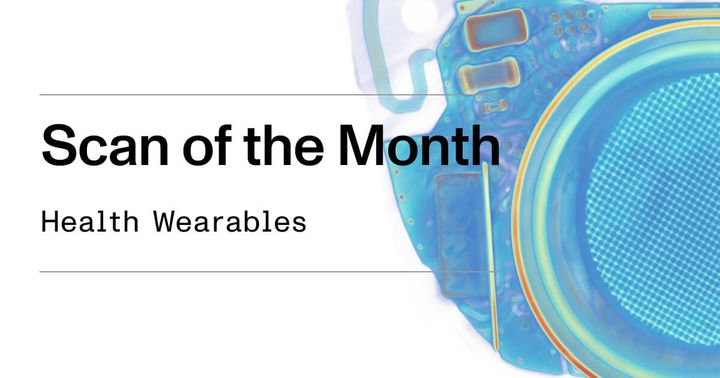
CT Scans of Health Wearables
This article explores the potential of health wearables to revolutionize personal healthcare, discussing their ability to continuously monitor various health metrics and provide valuable insights to users and medical professionals.
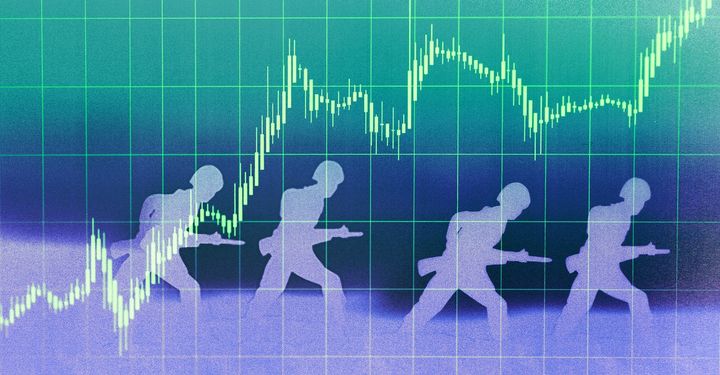
War prediction markets are a national-security threat
The article discusses the risks of insider trading in the prediction market Polymarket, which could have serious consequences for users. It highlights the need for stronger regulation and oversight to protect investors from potential harm.
Cloud VM benchmarks 2026
The article compares the performance and pricing of various cloud virtual machines, providing benchmarks and insights for users to make informed decisions about their cloud infrastructure needs.

Files are the interface humans and agents interact with
This article explores the importance of file systems in modern computing, highlighting their role in data storage, organization, and management. It discusses the evolution of file systems and the growing interest in understanding their impact on system performance and user experience.

We might all be AI engineers now
The article discusses the growing importance of AI in various industries and how more people are becoming AI engineers, even those without a traditional computer science background. It explores the increasing accessibility and widespread adoption of AI tools and platforms, allowing non-experts to participate in AI-related tasks and projects.
A tool that removes censorship from open-weight LLMs

FLASH radiotherapy's bold approach to cancer treatment
The article discusses the development of a new form of radiotherapy that uses ultrashort pulses of high-energy electrons to treat cancer tumors more precisely and with less collateral damage to surrounding healthy tissue compared to traditional radiation therapy.
QGIS 4.0
QGIS 4.0 introduces significant improvements to the user interface, data management capabilities, and analysis tools, aimed at enhancing the overall user experience for geographic information system professionals.
LLM Writing Tropes.md
The article provides an overview of tropes, which are commonly used narrative devices or patterns in stories, films, and other media. It explains the purpose and significance of tropes in creative works, and highlights how they can be used effectively to convey ideas, evoke emotions, and engage audiences.