Redox OS has adopted a Certificate of Origin policy and a strict no-LLM policy
The article outlines the contribution guidelines for the Redox operating system project, covering topics such as reporting issues, submitting patches, and code of conduct expectations for contributors.

Learnings from paying artists royalties for AI-generated art
The article discusses Kapwing's experience with paying royalties to artists whose work was used to train their AI model, highlighting the challenges and lessons learned in establishing a fair and sustainable model for compensating creators in the AI-generated art ecosystem.

Yann LeCun's AI startup raises $1B in Europe's largest ever seed round
The article explores the growing trend of 'quiet quitting,' where employees do the minimum required of their job and avoid going above and beyond. This shift in work culture is driven by factors like burnout, dissatisfaction with long hours, and a desire for a better work-life balance.

Windows: Microsoft broke the only thing that mattered
Microsoft has made significant changes to its Windows operating system, which has sparked controversy among users. The article discusses the company's decision to prioritize new features and design elements over the core user experience that many have come to rely on.

Amazon holds engineering meeting following AI-related outages
The article discusses the potential impact of artificial intelligence (AI) on the legal profession, highlighting concerns about AI's ability to automate certain legal tasks and the ethical challenges it poses in the field of law.
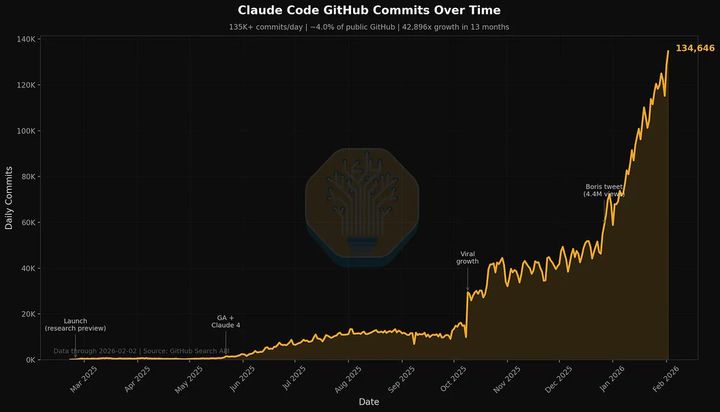
Claude Code, Claude Cowork and Codex #5
This article discusses the author's experience with Claude, an AI assistant, and its potential to revolutionize work and collaboration through features like code writing, task completion, and knowledge retrieval.
EVi, a Hard-Fork of Vim
Evi is an open-source, privacy-focused virtual assistant that aims to provide an alternative to Alexa, Siri, and other commercial AI assistants. It focuses on user privacy, local processing, and customizability, allowing users to train it on their own data and deploy it on their own infrastructure.

OpenClaw Did Not Just Go Viral in China, It Solved a Structural Problem
The article discusses OpenClaw, a comprehensive AI stack developed in China that aims to provide a full-stack solution for AI development and deployment. It explores the key features and components of the OpenClaw platform, which includes tools for data management, model training, and deployment.
Press-One: Auto-accept every Claude Code prompt
The article discusses the development of Press One, an open-source, decentralized social media platform that aims to provide users with more control over their data and content. It highlights the platform's focus on privacy, content moderation, and the use of blockchain technology to ensure transparency and user empowerment.

United States Leads Dismantlement of One of the Largest Hacker Forums
The United States Department of Justice announced the dismantling of one of the world's largest hacker forums, RaidForums, which was used to facilitate the buying and selling of stolen sensitive information and hacking tools.

Yann LeCun Raises $1B to Build AI That Understands the Physical World
Yann LeCun, the chief AI scientist at Meta (formerly Facebook), has raised $1 billion to launch a new AI research institute that will focus on developing AI systems that can better understand and interact with the physical world, bridging the gap between AI and the real-world environment.

Trump considering taking over Strait of Hormuz
The article discusses President Trump's comments on the ongoing tensions between the U.S. and Iran, particularly regarding the situation in the Strait of Hormuz. It highlights the president's assertion that the 'war is very complete' and provides context around the current state of the conflict.

Boredom Is the Price We Pay for Meaning
The article explores the impact of boredom on parenting, highlighting how it can lead to personal growth and stronger family bonds. It suggests that embracing boredom can foster creativity, empathy, and a deeper appreciation for the simple moments in parenting.
Too Much Color
The article discusses the use of excessive color in web design, highlighting how it can be overwhelming and detrimental to the user experience. It explores the importance of balance, contrast, and minimalism in creating visually appealing and accessible web interfaces.

Spanish Justice Summons Cloudflare CEO for Piracy Following LaLiga Lawsuit
The article discusses the Spanish justice system summoning Cloudflare, a content delivery network, to provide information related to a website allegedly involved in fraud. The article highlights the ongoing legal proceedings and Cloudflare's potential role in the investigation.

An iPhone-hacking toolkit used by Russian spies likely came from U.S. contractor
An iPhone hacking toolkit believed to have been used by Russian spies was likely developed by a U.S. military contractor, according to cybersecurity researchers. The toolkit, known as TRITON, was designed to target and exploit vulnerabilities in iOS devices.

Iran war shows Green Deal 'fundamental' to EU security
The article discusses the potential impact of the Russia-Ukraine war on the European Union's Green Deal and energy security goals, highlighting the EU's efforts to diversify energy sources and accelerate the transition to renewable energy in response to the crisis.

Breaking free from smartphone addiction: Defensive tactics against algorithms
The article explores strategies to reduce smartphone addiction, including setting boundaries, using screen time management tools, and understanding the psychological tactics employed by tech companies to keep users engaged. It provides practical tips for regaining control over digital habits and fostering a healthier relationship with technology.

A Swiss Paperwork Massacre: Why We Fled to Stripe
The article discusses the challenges faced by consumers and businesses due to payment processing issues, including delayed transactions, fraudulent activities, and the need for more secure and efficient payment solutions to address these problems.

Scotland becomes first UK country to legalise water cremations
Scotland has become the first UK country to legalize water cremations, also known as aquamation or alkaline hydrolysis. This environmentally-friendly alternative to traditional cremation uses water, heat, and alkaline chemicals to dissolve the body, reducing the carbon footprint and energy consumption of the cremation process.